The number of material on the net about creating LUKS partitions is surprisingly low. The few link I checked out only detailed how to setup permanent encrypted partitions that got mounted at every bootup. My requirement was to encrypt an external hard-drive that I use for backup purposes, therefore I set out to find out the process of encrypting a removable disk on my own. I was helped along the way by http://fedoraproject.org/wiki/Security_Guide/9/LUKSDiskEncryption and http://www.saout.de/tikiwiki/tiki-index.php?page=EncryptedDeviceUsingLUKS
Step 1:
Change in to the single user mode.
telinit 1
Step 2:
Check whether the drive is still mounted. (My drive is plugged in to /dev/sdb. Yours may vary)
mount | grep sdb
Unmount the drive if it is still mounted.
umount /dev/sdb
Step 3 (Optional):
For maximum security, the drive must be filled with random data. This can be done in two ways. Both methods are effective, but take a long time. You will possibly have to leave the process overnight to complete. Be warned; this step will OVERWRITE ALL DATA on the disk.
Method 1:
Use dd to write data from /dev/urandom. Make sure you type it correctly. If you type /dev/random by mistake, your grand-kids will be wrinkled and toothless by the time it finishes.
dd if=/dev/urandom of=/dev/sdb
Method 2:
Suggested by LUKS wiki. Kills two birds with one stone by writing random data to the disk and checking it for errors at the same time.
badblocks -c 10240 -s -w -t random -v /dev/sdb
Step 4:
Create the LUKS partition.
cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb
Step 5:
Load the logical encrypted device.
cryptsetup luksOpen /dev/sdb my_enc_drive
This command will create /dev/mappers/my_enc_drive. You can provide any name you like in place of "my_enc_drive". To check whether the command succeeded, type:
ls -l /dev/mappers
You should see a new entry titled "my_enc_drive" in the output.
Step 6:
Create the file system. You can choose any file system you like. Be aware of permission problems when using secure file systems such as ext3. In this case, I am creating an ext3 file system on the encrypted disk.
mkfs.ext3 /dev/mapper/my_enc_drive
Step 7:
Mount the drive.
mount -t ext3 /dev/mapper/my_enc_drive /media/my_enc_drive
If everything went successfully, your encrypted file system is ready now. Reboot the computer to bring up the desktop and plug the drive in. It is automatically recognized as an encrypted drive and you will be prompted for a password.
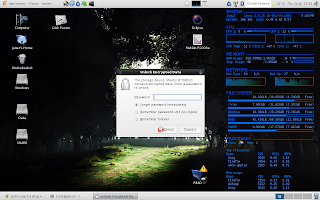
In theory, the drive should be mounted automatically after you enter the password. But on my machine, the entry to /dev/mapper was automatically created, but the drive wasn't mounted automatically. I still haven't found the reason for this behaviour, but it is only a minor setback. The drive can be used without any problem by manually mounting it.
sudo mount -t ext3 /dev/mapper/luks_crypto_8e8d6392-7be3-4964-8e6d-9de57e886fa5 /media/my_enc_drive
" luks_crypto_8e8d6392-7be3-4964-8e6d-9de57e886fa5" is the name automatically generated by the HAL daemon. Yours will definitely be different.
To unmount the drive after using it. Simply type:
sudo umount /media/my_enc_drive
sudo cryptsetup luksClose luks_crypto_8e8d6392-7be3-4964-8e6d-9de57e886fa5
LUKS can be a viable alternative to TrueCrypt. The disk access speeds seem much better compared to TrueCrypt, at least on my machine. Best of all, LUKS comes pre-installed with Fedora 9. Therefore you don't need to struggle with getting the sources and compiling TrueCrypt.
